Subordinate CA
Introduction
Create CA Hierarchy Lab Overview - PART 2, Create the Subordinate CA
Slide Deck: Create CA Hierarchy
Overview: This lab is used to create our EJBCA PKI Hierarchy lab environment, which will be used throughout this course.
The Create CA Hierarchy consists of three parts; creating a Root CA, a Subordinate CA, and an External Subordinate CA.
The second part of this lab focuses on creating the Subordinate CA. This section is very similar to creating the Root CA in the previous section.
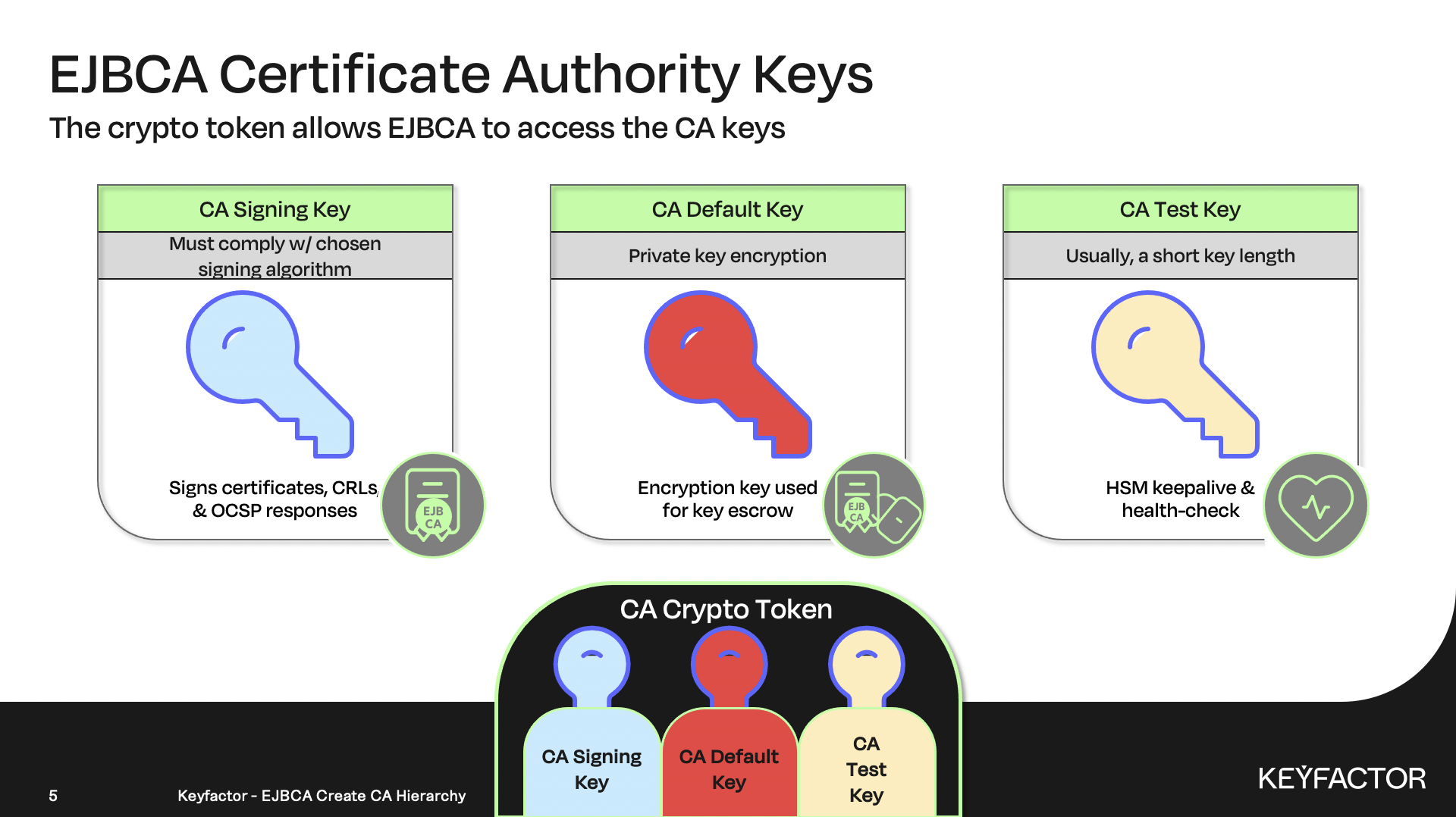
Create a Crypto Token which allows EJBCA to access the Subordinate CA keys.
Clone the SUBCA certificate profile, which is provided as a template with EJBCA, and make modifications required for the lab environment i.e. select key algorithm, and key length etc.
Create the Subordinate CA, by making modifications specific for the Subordinate CA, adding any asserted information, i.e. DN of the CA, assign the crypto keys to their usage, and configure CRL validity periods.
Slide Reference
Create the crypto token first
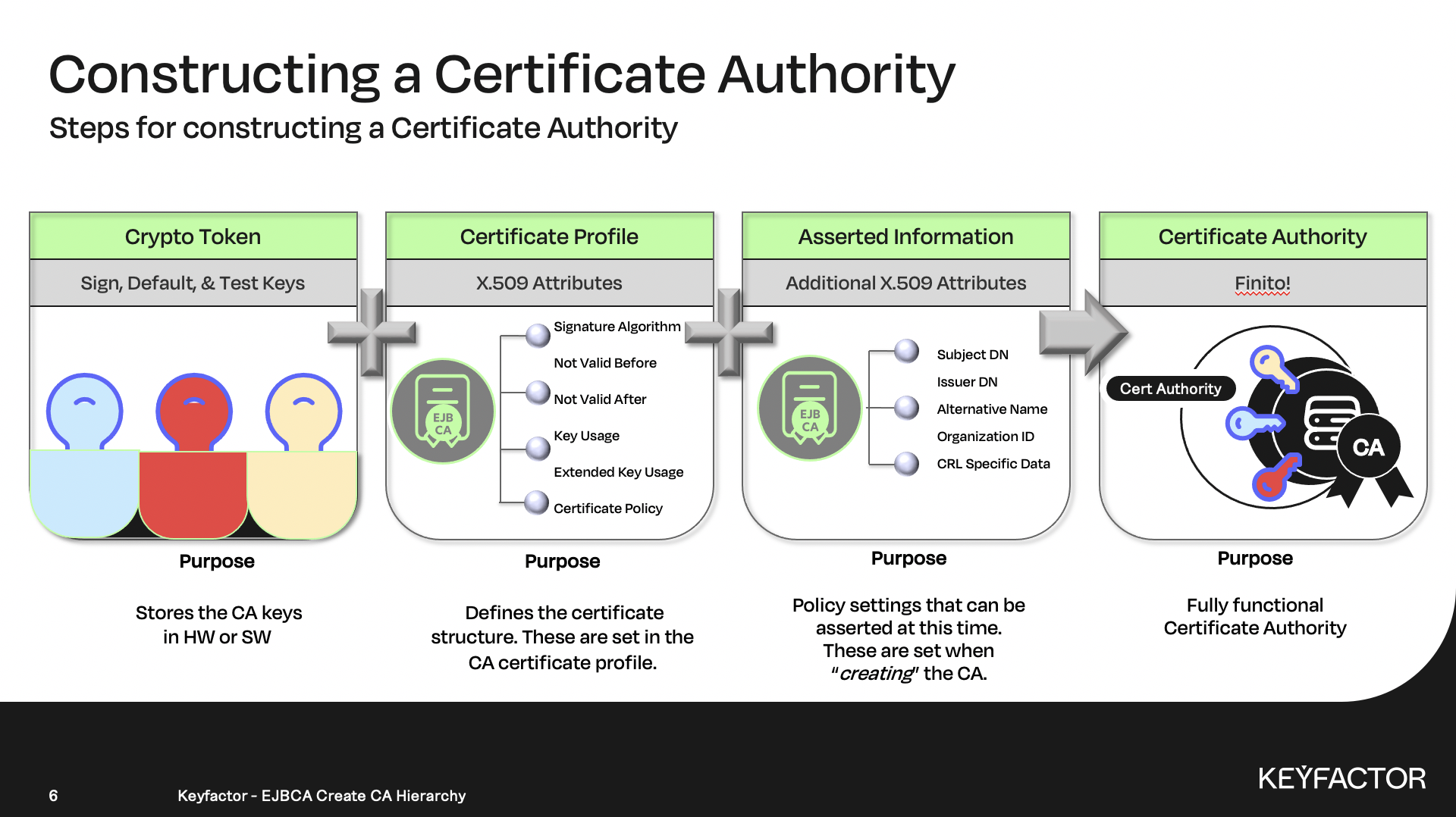
Next create the certificate authority
Create Subordinate CA Crypto Token
Click CA Functions >> Crypto Tokens
Click Create new
In the Name field, enter subcacryptotoken
In the Type list, select PKCS#11 NG
Click the Auto Activation checkbox, to enable the crypto-token to auto-activate
In the PKCS#11 Library list, select P11 Proxy if not already selected
In the PKCS#11 Reference Type list, select Slot/Token Label
In the PKCS#11 Reference list, select SUB_CA_SLOT
In the Authentication Code field, enter the password for the slot (password on the training system is foo123)
In the Repeat Authentication Code field, re-enter the password from previous step
Click Save
Enter signKey00001 as the name for the new key, choose RSA 4096 from the list, select Sign and Encrypt for key usage and click Generate new key pair
Click Test for the new key created, the result should be signKey00001 tested successfully
Enter defaultKey00001 as the name for the new key, choose RSA 4096 from the list, select Sign and Encrypt for key usage, and click Generate new key pair
Click Test for the new key created, the result should be defaultKey00001 tested successfully
Enter testKey as the name for the new key, choose RSA 1024 from the list, select Sign and Encrypt for key usage, and click Generate new key pair
Click Test for the new key created, the result should be testKey tested successfully
Create Subordinate CA Certificate Profile
Click CA Functions >> Certificate Profiles
On SUBCA click Clone
Enter SubCACertificateProfile and click Create from template
Click Edit on the profile SubCACertificateProfile
In the Available key algorithms list, select RSA
In the Available bit lengths list, select 4096 bits
In the Signature Algorithm list, select SHA256WithRSA
In the Validity field, enter 10y 3mo
Uncheck the Subject Alternative Name Use... checkbox
Uncheck the Issuer Alternative Name Use... checkbox
Uncheck the LDAP DN order checkbox
In the Available CAs list, select Root CA
Keep the other values as default
Click Save
Create Subordinate CA
Click CA Functions >> Certification Authorities
In the Add CA field, enter Sub CA and click Create…
In the Crypto Token list, select subcacryptotoken
In the defaultKey list, select defaultKey00001
In the certSignKey list, select signKey00001
In the testKey list, select testKey
In the Subject DN field, enter CN=Sub CA,O=PrimeKey Solutions AB,C=SE
In the Signed By list, select Root CA
In the Certificate Profile list, select SubCACertificateProfile
In the Validity field, enter 10y 3mo
In the Certificate Policy OID field, enter 2.5.29.32.0 or insert your organization OID
In the LDAP DN Order, uncheck the checkbox
In the CRL Expire Period field, enter 2d
In the CRL Issue Interval field, enter 1d
In the CRL Overlap Time field, enter 0m
In the Monitor if CA active (healthcheck), check Activate
Click Create
%20(500%20x%20162%20px)(1).png)